Businesses nowadays increasingly find themselves targeted by phishing emails or scams. Cyber criminals send phishing emails to organization’s employees to get confidential information or sensitive data or to deliver a ransomware payload.
Attackers send attached malicious payloads with emails and the moment the user downloads the attached malicious files, all the data stored in her computer gets encrypted and the computer gets the message of paying ransom in cryptocurrency (mostly in bitcoins).
Recently big IT giant Cognizant faced a massive ransomware attack and possibilities are there that attackers used phishing email to deliver the ransomware payload.
At present the investigation is in process and putting assumptions is not a good idea at all.
What is a phishing attack ?
Phishing attack is a kind of social engineering attack, that gives a cyber criminal scale and ability to target thousands of users at once.
Phishing emails/scams involves sending out emails with malicious links or attachments or texts disguised as legitimate sources.
These emails look like they come from trusted vendors or government authority but stealthily they contain malware.
Phishing emails are designed to trick the victim into opening the email through the tactics of fear and intimidation.
Once the person opens the email and the attached malicious payload downloads and installs itself and the cyber criminal gets control of your computer system.
Cyber criminals use common social engineering methods including sending emails with embedded URLs. User clicks on the URL and redirects the user to the phishing site.
Phishing emails are the easiest way to execute any cyber attack. Most of the organizations prepare themselves for the external cyber attacks but very few are ready to combat an social engineering attack like Phishing scam.
Aristi simulated phishing test service will help your organization prepare for phishing scams and other social engineering attacks.
Types of Phishing attacks
Email Phishing Scam :
It’s a number game, cyber criminals send thousands of fraudulent emails. This can get significant amounts of information/data and money even if a small percentage of people fall for the scam.
Cyber criminals design phishing emails to mimic legitimate emails from a spoofed organization. They use the same phrasing, typefaces, logos, and signature to make the email look actual.
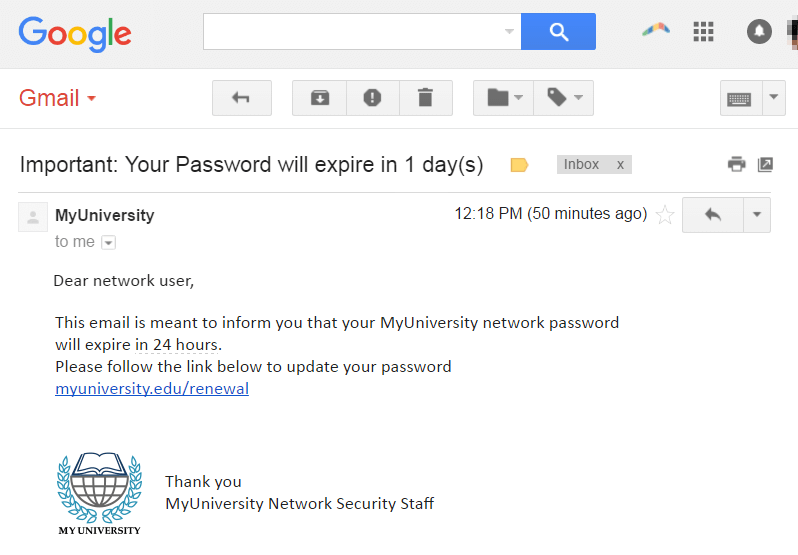
In addition, cyber criminals try to create a sense of urgency into their scam emails. For example, as earlier shown in the email, cyber criminals threaten account expiration within 24 hours.
Applying such pressure causes the user to be less diligent and more prone to fall for the scam.
Lastly, links inside scam emails resemble their legitimate counterparts, but typically have misspelled or similar domain names or sub domains.
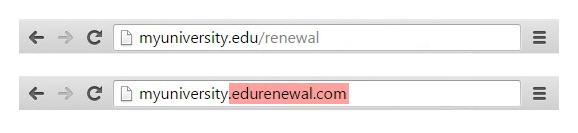
In the above example, myuniversity.edu/renewal URL was changed to myuniversity.edurenewal.com. Which looks pretty much legitimate and less aware recipient can easily fall for the scam.
Spear Phishing Scam:
Spear phishing scams targets a specific person or organization. It’s a more advanced version of phishing attack that requires detailed information about an enterprise, including it’s business or power structure.
An spear phishing attack might play out as follows:
1. A cyber criminal identifies the name of employees of an organization’s marketing department using social media and other intelligence gathering techniques to get the latest project invoice.
2. Cyber criminal can send an email using the name of the marketing director of the company to the project manager using the subject line that reads, Updated invoices for Q2 campaigns. The text, style and logo looks similar to the company’s standard email template.
3. A link in the email redirects to a password-protected confidential document, which is in reality a spoofed version of a stolen invoice.
4. The project manager log-in to view the document and shares her credentials. Cyber criminal steals his credentials and gets the full access of the business critical and confidential documents of the organization.
By providing valid credentials to the cyber criminal, spear phishing is a very effective method of executing the first stage of Advanced Persistent Attack (APT Attack).
How to protect yourself and business from phishing attacks?
Educate your employees :
Educated and well aware employees are the best defense against phishing scams and any other type of cyber attacks. It does not matter if you have the best spam email detection technology in the world.
Cyber criminals are very clever and they can bypass any security. Plus, an unaware employee can also fall in other types of scams such as phone scam or vishing.
Do not share a lot of information :
Be Aware before sharing your sensitive personal and business information. Nowadays we have tons of social media accounts and we do not hesitate giving out our email address and phone numbers.
We know even big giants are facing massive data breaches, if your business critical and confidential information is made public due to any such data breach.
you may easily become victim of email scams as not cyber criminals have a lot of information about yourself and they can easily trap you.
Conduct simulated phishing test :
Experience is the best teacher but for that you don’t need to become the victim of a real phishing attack.
Hire Aristi simulated phishing test service, we will conduct a real world phishing attack on your organization without the real world loss.
Simulated phishing test will give your employees pragmatic experience in identifying and responding to phishing scams.
Have a cybersecurity policy in place :
Make sure your business has a cybersecurity policy. Establish guidelines how employees should use technology in and outside the workspace.
You can deploy ISO27001 ISMS into your organization for better management of IT and IT security into your organization.
For any cybersecurity related assistance please feel free to contact Aristi.

